FabCon is coming to Atlanta
Join us at FabCon Atlanta from March 16 - 20, 2026, for the ultimate Fabric, Power BI, AI and SQL community-led event. Save $200 with code FABCOMM.
Register now!- Power BI forums
- Get Help with Power BI
- Desktop
- Service
- Report Server
- Power Query
- Mobile Apps
- Developer
- DAX Commands and Tips
- Custom Visuals Development Discussion
- Health and Life Sciences
- Power BI Spanish forums
- Translated Spanish Desktop
- Training and Consulting
- Instructor Led Training
- Dashboard in a Day for Women, by Women
- Galleries
- Data Stories Gallery
- Themes Gallery
- Contests Gallery
- QuickViz Gallery
- Quick Measures Gallery
- Visual Calculations Gallery
- Notebook Gallery
- Translytical Task Flow Gallery
- TMDL Gallery
- R Script Showcase
- Webinars and Video Gallery
- Ideas
- Custom Visuals Ideas (read-only)
- Issues
- Issues
- Events
- Upcoming Events
Learn from the best! Meet the four finalists headed to the FINALS of the Power BI Dataviz World Championships! Register now
- Power BI forums
- Forums
- Get Help with Power BI
- Developer
- How to implement getNewUserAccessToken() function ...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to implement getNewUserAccessToken() function for PowerBI embedded
On Microsoft docs you can find an example how to refresh the powerbiembedded token to overcome the 1 hour lifetime.
Refresh the access token in Power BI embedded analytics | Microsoft Docs
However this note seems to be the key to the solution
===========================
Note
getNewUserAccessToken() is a function you need to implement, it calls your application back-end for generating a new embed token, or refreshes the Azure AD token.
===========================
I tried several things to create that getNewUserAccessToken() function, but don't know how to do it and cannot find the right solution until now.
Is there anyone who already has successfull implemented this?
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Anonymous , I have created the PowerBI embedded by using creating a portal using the Power Platform. There I used the procedure mentioned here: Set up Power BI integration - Power Apps | Microsoft Docs
It was not possible to create the refresh token, because the token aquisition is done by the Power Platform.
However it was possible to extend the tokenlifetime by creating an Azure AD policy and assign it to the Power BI service account. I was struggling with it because I tried to extend the tokenlifetime of the PowerApp account that was registered in my tenant, that didn't solve the issue. The embedded PowerBI session still expired after hour.
Below the PowerShell script that I have used to extend the token lifetime to 23 hours and it works as expected.
# Login
Connect-AzureAD
Get-AzureADServicePrincipal -filter "DisplayName eq 'Power BI Service'" -Verbose
#Define policy for 23 hours
$policy = New-AzureADPolicy -Definition @('{"TokenLifetimePolicy":{"Version":1,"AccessTokenLifetime":"23:00:00"}}') -DisplayName "PowerBI-access-token-Policy" -IsOrganizationDefault $false -Type "TokenLifetimePolicy"
# Get ID of the service principal
$sp = Get-AzureADServicePrincipal -Filter "DisplayName eq 'Power BI Service'"
# Assign policy to the id of the service principal found in the previous step
Add-AzureADServicePrincipalPolicy -Id $sp.ObjectId -RefObjectId $policy.id
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The reply marked as the solution doesn't do what the OP asked for -- refreshing the access token. It's a different approach, extending the lifetime of the original access token. It's frustrating coming to this page looking for help on how to refresh the access token, and the 'solution' is something totally different -- and something that doesn't work in all situations.
I'd encourage moderators to not allow marking a question 'solved' when it has not, in fact, been solved. The answer is at best a workaround that achieves the same goal, without ever answering the original question. The OP asked for how to implement getNewUserAccessToken(), specifically. The 'answer' is something else entirely.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Anonymous @Anonymous
I've created in another post a related but different topic you could give me a hand with and I'd make you a monument!
Here is the post:
https://community.powerbi.com/t5/Developer/Refresh-the-token-in-PowerBI-Embedded/m-p/2548512#M36427
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Anonymous ,
Please review the content in the following links, hope they can help you.
1. Get access token by postman or programming with C#
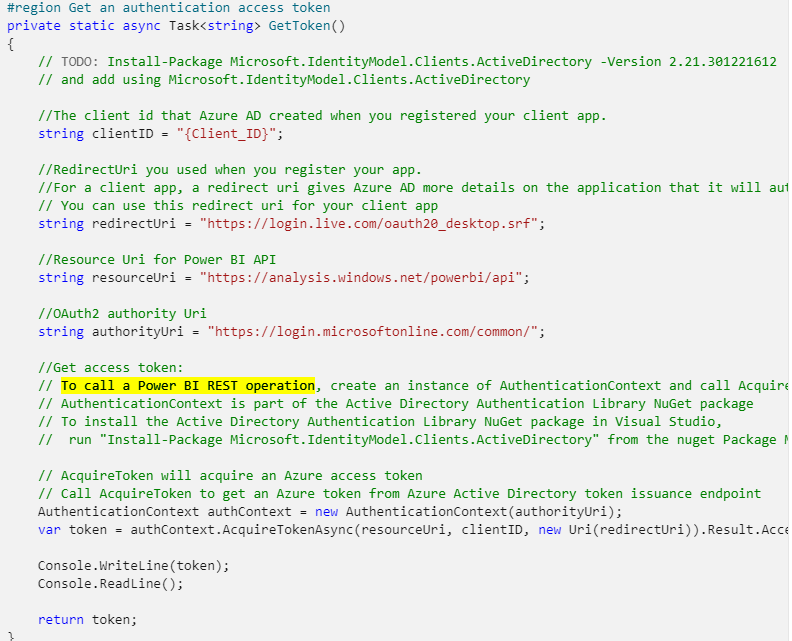
2. Get an Azure AD access token for your Power BI application
3. Get access token by Phython
Best Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Anonymous , I have created the PowerBI embedded by using creating a portal using the Power Platform. There I used the procedure mentioned here: Set up Power BI integration - Power Apps | Microsoft Docs
It was not possible to create the refresh token, because the token aquisition is done by the Power Platform.
However it was possible to extend the tokenlifetime by creating an Azure AD policy and assign it to the Power BI service account. I was struggling with it because I tried to extend the tokenlifetime of the PowerApp account that was registered in my tenant, that didn't solve the issue. The embedded PowerBI session still expired after hour.
Below the PowerShell script that I have used to extend the token lifetime to 23 hours and it works as expected.
# Login
Connect-AzureAD
Get-AzureADServicePrincipal -filter "DisplayName eq 'Power BI Service'" -Verbose
#Define policy for 23 hours
$policy = New-AzureADPolicy -Definition @('{"TokenLifetimePolicy":{"Version":1,"AccessTokenLifetime":"23:00:00"}}') -DisplayName "PowerBI-access-token-Policy" -IsOrganizationDefault $false -Type "TokenLifetimePolicy"
# Get ID of the service principal
$sp = Get-AzureADServicePrincipal -Filter "DisplayName eq 'Power BI Service'"
# Assign policy to the id of the service principal found in the previous step
Add-AzureADServicePrincipalPolicy -Id $sp.ObjectId -RefObjectId $policy.id
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Anonymous ,
It's glad to hear that your problem has been resolved. And thanks a lot for sharing the solution here, it will help the others in the community get the solution easily if they face the same problem with you. Much appreciated!
Best Regards
Helpful resources

Join our Fabric User Panel
Share feedback directly with Fabric product managers, participate in targeted research studies and influence the Fabric roadmap.

Power BI Monthly Update - February 2026
Check out the February 2026 Power BI update to learn about new features.

| User | Count |
|---|---|
| 3 | |
| 3 | |
| 2 | |
| 1 | |
| 1 |
| User | Count |
|---|---|
| 5 | |
| 4 | |
| 3 | |
| 3 | |
| 2 |