Join us at FabCon Vienna from September 15-18, 2025
The ultimate Fabric, Power BI, SQL, and AI community-led learning event. Save €200 with code FABCOMM.
Get registered- Power BI forums
- Get Help with Power BI
- Desktop
- Service
- Report Server
- Power Query
- Mobile Apps
- Developer
- DAX Commands and Tips
- Custom Visuals Development Discussion
- Health and Life Sciences
- Power BI Spanish forums
- Translated Spanish Desktop
- Training and Consulting
- Instructor Led Training
- Dashboard in a Day for Women, by Women
- Galleries
- Data Stories Gallery
- Themes Gallery
- Contests Gallery
- Quick Measures Gallery
- Notebook Gallery
- Translytical Task Flow Gallery
- TMDL Gallery
- R Script Showcase
- Webinars and Video Gallery
- Ideas
- Custom Visuals Ideas (read-only)
- Issues
- Issues
- Events
- Upcoming Events
Compete to become Power BI Data Viz World Champion! First round ends August 18th. Get started.
- Power BI forums
- Forums
- Get Help with Power BI
- Developer
- For Azure Support team: What permissions are requi...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
For Azure Support team: What permissions are required to generate a PBI Embedded token?
Azure Support asked me to post this issue here so they could have the details; however, if anyone else has a recommendation, please let me know.
Moderator: This is a re-post from earlier this morning. For some reason, this was marked as spam and removed. No idea why, but please leave this up so Azure Support can help solve the issue. Thanks.
We've been using Power BI since late 2016, and in particular, Power BI Embedded. We started with the PBI Embedded Workspace Collection, and we're working on migrating to Power BI Embedded. After struggling for a while, we're nearly done; however, there's one last issue that has been giving us headaches: generating an embed token for an account other than my own. So, we can generate the token and render the PBI Embedded report when using my credentials, but not when using a different account (no way we're rolling anything to production with client users impersonating my account!).
Here's our setup (we're using Power BI Embedded in the "ISV scenario" - external clients):
Azure
- Environment uses AD, and is synced to AAD. My account, and the second account are global admins (I'll dial that back as soon as I know that's not the issue).
- In Azure, I created the Power BI Embedded (A1) resource, and I set the Access Control so my account and another account are admins/owners. The resource is running.
- On https://dev.powerbi.com/apps, I setup the App Registration with appropriate permissions for this report. On Azure, I updated the owners and required permissions (for the API calls) so the second account has the exact same permissions as my account (I even clicked the "grant permissions" button to ensure the permissions propagated).
- For AAD, I went to Enterprise Applications, found the App Registration I created, and then added my acount and the second account as users (default access). I also verified that Power BI API permissions are set as needed (Permissions). I'm not sure if that was necessary, but I was grasping at straws, so why not, right?
Power BI
- Using my account on powerbi.com (Power BI Pro license), I created the reporting workspace for the migrated report.
- The PBI Report we're migrating was developed using PBI Desktop. I used my account to publish it to this new workspace on powerbi.com.
- I edited the workspace to make an additional user account an admin for that workspace. That user account also has a Power BI Pro license assigned.
- The workspace has been edited so it uses the dedicated capacity on Azure that I created earlier.
- The second account is the same between Azure and Power BI (obviously).
I have watched many of the videos from Adam Saxton (Microsoft/GuyInACube), and read numerous articles. Adam was even kind enough to reply to some of my tweets to try to help me. At this point, I'm stuck. We can use my account for the moment, but we really need to change the ownership over to this second account. I should be able to assign this account as an admin, and have it work, but that doesn't seem to be the case. We keep getting an error on the permissions when creating the token and rendering the report. Works for my account, but not the second account. What am I missing?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What is the actual error? I didn't see that listed.
From the sounds of it though, it has to do with the permissions on the App registration. You indicated you did do the Grant Permission step, which was the first thing I thought was missed when reading this initially, but you said you did it. and it works for your account. I'm assuming you performed the Grant Permissions step with your account.
I'm also going to assume that your account is not a Global Admin of the tenant. Let me know if that assumption is incorrect.
If you perform Grant Permission with a non-Global Admin account, it only performs that Grant Permission action on the account signed in. Meaning if you want other accounts to be able to use it as well, they would also need to do the Grant Permission action to pre-consent for their accounts. If you perform the Grant Permission step with a Global Admin account, it will pre-consent every account within the tenant and my guess is you would not have seen a problem.
The guidance in the documentation is to either perform the Grant Permission step with the account that will be doing the embedding or to do it with a Global Admin account. There is also the following blurb listed for Step 6 of performing these steps in the Azure AD portal:
The Grant Permissions action is needed for the master account to avoid being prompted for consent by Azure AD. If the account performing this action is a Global Admin, you will grant permissions to all users within your organization for this application. If the account performing this action is the master account and is not a Global Admin, you will grant permissions only to the master account for this application.
Let me know if that doesn't align with what you have done, or doesn't make sense.
@GuyInACube | youtube.com/guyinacube
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Adam!
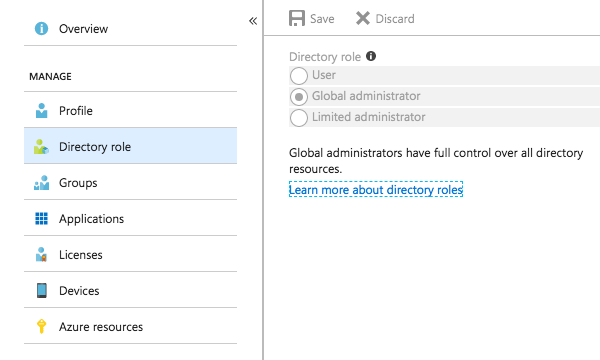
Thanks so much for popping into this thread! It was a good assumption, but actually, my account is a global administrator. See the screenshot I just took from the Azure portal (below).
Now, the second account is also a Global administrator. Should that account login and grant itself permissions? Based on what you said, it shouldn't be necessary, but is that worth verifying?
Also, I can grab and post screenshots of my other settings. I'd only have to edit them to remove any confidential info. If you think that's help, let me know which screenshots would be helpful.
Thanks again!!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
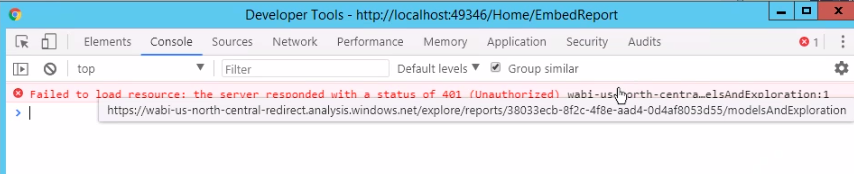
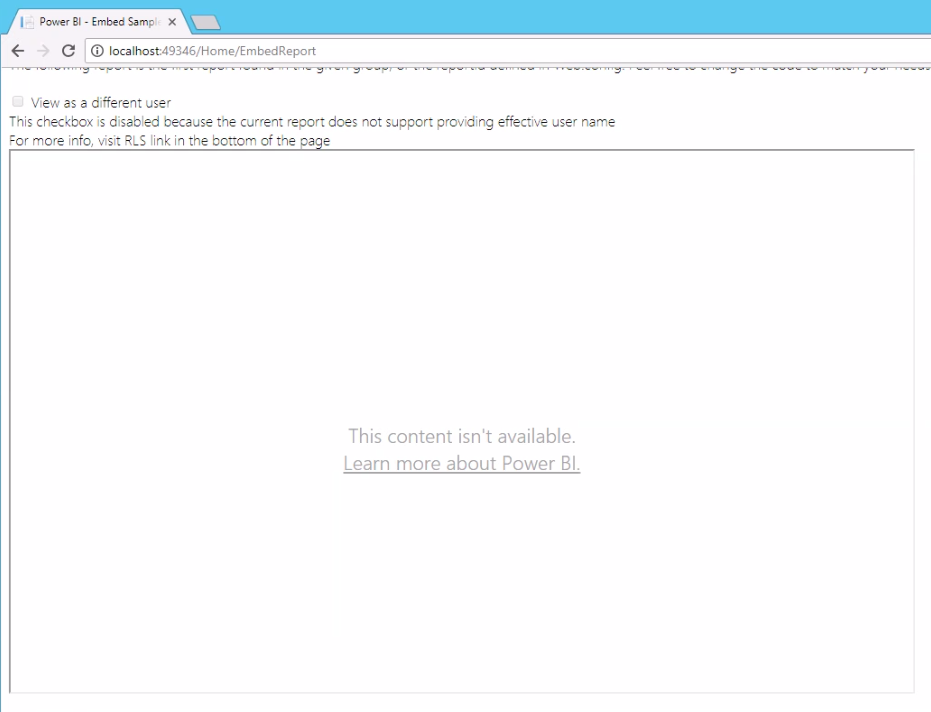
I have an update from my dev team. They are getting an embed token when using the second ID; however, the report isn't rendering, and they're getting a 401. Here are two screenshots:
When they switch to my account, the report renders. Also, just to double check, the Group ID is in the URL for the report while looking at it in powerbi.com, right? I seem to recall your video saying that. The URL also includes the Report ID.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ah! that's helpful. i thought you were getting a 401 on the GenerateToken call. So, if you are getting a 401 when trying to embed a report, the master account being used doesn't have access to the report or the App workspace, or isn't an admin of the app workspace. It's a permission issue. They should be an admin of the app workspace where that report is published to.
@GuyInACube | youtube.com/guyinacube
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I got it working!! There are a lot of touch points for permissions, and security. I am going to write a post here, along with diagrams. The short story is that I removed other test users from Azure and Power BI. Then I created the special "master" account that all users will impersonate for the Power BI Embedded reports. I gave that user a Power BI Pro license, but no other licenses (e.g., nothing from Office 365). From my personal powerbi.com account (Pro license), I made sure to make this new master account an Admin for the Workspace and I shared the report with that new user. I then logged into powerbi.com with this new master account, and verified that I could access the report and that I had admin permissions.
Now, as I said, there are number of permissions touch points in Azure. I'm not 100% sure that all of them are required, but I decided to add access for the new master account anyway. I'll write up a proper post tomorrow.
I'm going to reiterate that setting up Power BI Embedded is far more complicated than it needs to be. Version 2 of PBI Embedded still feels like a solution that was cobbled together instead of a more mature, integrated solution.
More to follow, but thanks to Adam/GuyInACube & KalberPowerBI for the help!!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Correct. That is what I was stating previously. The Grant Permission step is required from the App registration permission and has to be applied to the "master" account (whatever user account that is being used) as indicated above. That "master" account needs to be an admin of the app workspace where the content is being embedded from. The master account also requires a Power BI Pro license.
Doesn't matter what account is used, It just needs to have all of the above applied.
@GuyInACube | youtube.com/guyinacube
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Have you forced the new account to login by going through the Grant Permissions step?
I would force the embed page to bring up the Grant Permissions page and use your new "master" account credentials:
authenticationResult = await authenticationContext.AcquireTokenAsync(
ResourceUrl,
ClientId,
new Uri("youruriendpoint"),
new PlatformParameters(PromptBehavior.Always));
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Have you forced the new account to login by going through the Grant Permissions step?
You can force the embed page to bring up the Grant Permissions page with the following snippet:
authenticationResult = await authenticationContext.AcquireTokenAsync(
ResourceUrl,
ClientId,
new Uri("uriendpoint"),
new PlatformParameters(PromptBehavior.Always));