FabCon is coming to Atlanta
Join us at FabCon Atlanta from March 16 - 20, 2026, for the ultimate Fabric, Power BI, AI and SQL community-led event. Save $200 with code FABCOMM.
Register now!- Power BI forums
- Get Help with Power BI
- Desktop
- Service
- Report Server
- Power Query
- Mobile Apps
- Developer
- DAX Commands and Tips
- Custom Visuals Development Discussion
- Health and Life Sciences
- Power BI Spanish forums
- Translated Spanish Desktop
- Training and Consulting
- Instructor Led Training
- Dashboard in a Day for Women, by Women
- Galleries
- Data Stories Gallery
- Themes Gallery
- Contests Gallery
- QuickViz Gallery
- Quick Measures Gallery
- Visual Calculations Gallery
- Notebook Gallery
- Translytical Task Flow Gallery
- TMDL Gallery
- R Script Showcase
- Webinars and Video Gallery
- Ideas
- Custom Visuals Ideas (read-only)
- Issues
- Issues
- Events
- Upcoming Events
The Power BI Data Visualization World Championships is back! Get ahead of the game and start preparing now! Learn more
- Power BI forums
- Forums
- Get Help with Power BI
- Developer
- Re: Attempt to get list of Workspaces via REST API...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Attempt to get list of Workspaces via REST API results in 401 Unauthorized.
I'm currently using the REST API to list Datasets. This is working just fine. Now, I want to get a list of Workspaces (that my user has access to). To do this, I'm using the call here: https://docs.microsoft.com/en-us/rest/api/power-bi/groups/get-groups
The problem is, I get this error: "The remote server returned an error: (401) Unauthorized."
I went into Azure and updated the permissions for my app to include: Workspace.ReadWrite.All
...but still no dice. I'm using the same code to get my auth header that I use when getting a list of Datasets. Everything else is the same code as well. The only thing I'm changing is the URL for the API call. What else do I need to do to enable this?
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I finally found the answer to this issue and wanted to document it here.
The issue is that you don't need to just add API Permissions to an App Registration. You need to also consent to each API Permission (scope) at a user or app level. Now, an admin can grant access for all users (which is what is mentioned by some answers here in this post), but I'm not an admin, so I couldn't do that. What I needed to do was consent as a user to the specific API permissions that I had added to my App Registration.
Unfortunately, I couldn't find a way to do this in the Azure AD interface. In fact, I only found one place anywhere that actually explained how to do this for a *user* (the admin-level consent was mentioned in numerous places). Here is an answer here which talks about the URL needed to grant user consent to an API permission: https://stackoverflow.com/questions/59282141/aadsts65001-the-user-or-administrator-has-not-consented...
The URLs look like so:
https://login.microsoftonline.com/[Put your Tenant ID here]/oauth2/v2.0/authorize? client_id=[This is your Client ID from your App Registration] &response_type=code &redirect_uri=https://myapp.mycompany.com[This must be the Redirect URI you setup in your App Registration] &response_mode=query &scope=https://graph.microsoft.com/User.Read[This is the scope URL for the API Permission]
Once I (finally) found that example, I was able to piece together a URL to consent to the newly added Workspace API permissions and my code started working. You can find out the "scope" URL for each API permission (which you have to add to the end of the full URL above) by going to your App Registration and clicking on API Permissions and then clicking on any of the API permissions you've added. This will bring up a window which shows the URL for that API Permission.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I finally found the answer to this issue and wanted to document it here.
The issue is that you don't need to just add API Permissions to an App Registration. You need to also consent to each API Permission (scope) at a user or app level. Now, an admin can grant access for all users (which is what is mentioned by some answers here in this post), but I'm not an admin, so I couldn't do that. What I needed to do was consent as a user to the specific API permissions that I had added to my App Registration.
Unfortunately, I couldn't find a way to do this in the Azure AD interface. In fact, I only found one place anywhere that actually explained how to do this for a *user* (the admin-level consent was mentioned in numerous places). Here is an answer here which talks about the URL needed to grant user consent to an API permission: https://stackoverflow.com/questions/59282141/aadsts65001-the-user-or-administrator-has-not-consented...
The URLs look like so:
https://login.microsoftonline.com/[Put your Tenant ID here]/oauth2/v2.0/authorize? client_id=[This is your Client ID from your App Registration] &response_type=code &redirect_uri=https://myapp.mycompany.com[This must be the Redirect URI you setup in your App Registration] &response_mode=query &scope=https://graph.microsoft.com/User.Read[This is the scope URL for the API Permission]
Once I (finally) found that example, I was able to piece together a URL to consent to the newly added Workspace API permissions and my code started working. You can find out the "scope" URL for each API permission (which you have to add to the end of the full URL above) by going to your App Registration and clicking on API Permissions and then clicking on any of the API permissions you've added. This will bring up a window which shows the URL for that API Permission.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In the error response, did you get a message about performing an "interactive" request for admin consent?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
No. The entire message I get is: "The remote server returned an error: (401) Unauthorized."
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ok. When you added the new Scope to you app, perhaps it is not Admin Consented to the User that you are trying to use. Try this...
In Azure Active Directory
- Go to Users, Select your user
- Click Applications on the Left
- Click the Application in the list that has the new Scope you just added
- You will see an Assignment Detail screen... at the bottom, click View Granted Permissions
- You will see a Permissions & Content screen... Search the list to make sure the new scope is in the list granted to your user. If not, add it now and try again.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I think we're getting somewhere, but I still can't fix it.
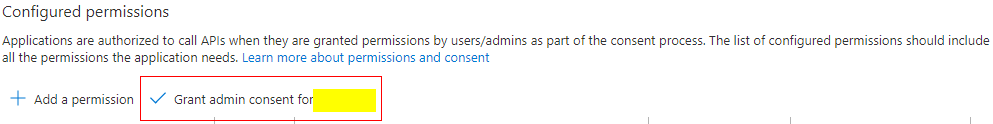
When I click on View Granted Permissions I see a big button that says "Grant Admin consent for [My Company]" which, if I'm reading the description correctly, grants access to that app for all users, not just a specific user. So I don't want that.
Then below that I see a couple tabs: Admin consent and User constent.
The Admin tab is empty (no permissions have been granted by an admin), but when I go to the User consent tab, I see permissions granted to that user, but I only see "Read and write all datasets". I don't see "Read and write all Workspaces" even though I've added that permission to the app. And there's no "Add" button anywhere I can see to add new permissions. Isn't that permission added at the app level?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Finally found an answer to this (exceptionally poorly documented) process. See below.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Anonymous
Please check whether you have grant admin consent in your API Permission.
Here are two posts with similar errors like yours.
For reference:
Power Bi REST API - 401 Authorization error when using Service Principals
Power Bi REST API - 401 Authorization error when using app secret
Best Regards,
Rico Zhou
If this post helps, then please consider Accept it as the solution to help the other members find it more quickly.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That "Grant admin consent for..." checkbox is grayed out on my screen.
And I looked at those other posts, but they're for Tenant access, not Workspace access, and I don't even follow what they mean about a "Service Principle". I'd need more detail to even try to implement those solutions.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Anonymous
Can you see green icon "Granted for ..." on the right side of "Workspace..." as below? If you couldn't see green icon, the admin hasn't grant consent for it. That "Grant admin consent for..." checkbox is grayed out on your screen.
Please refer to blog as below for more details about "Grant admin consent for..." function.
For reference: Enable the admin consent workflow
Best Regards,
Rico Zhou
If this post helps, then please consider Accept it as the solution to help the other members find it more quickly.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Also, I tried that link you posted, but I don't have rights to those options, so they're all grayed out.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Anonymous
App owns data (Service principal) doesn't need you to add api permission.
What kind of App did you register in Azure Portal, app owns data (master user) or user owns data?
Please check your app, and the parameter you use in request body.
For reference:
Register an Azure AD application to use with Power BI
Here I found some post with
Power Bi REST API - 401 Authorization error when using Service Principals
Power Bi REST API - 401 Authorization error when using app secret
Best Regards,
Rico Zhou
If this post helps, then please consider Accept it as the solution to help the other members find it more quickly.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm not sure what you mean by this:
"App owns data (Service principal) doesn't need you to add api permission. What kind of App did you register in Azure Portal, app owns data (master user) or user owns data? Please check your app, and the parameter you use in request body."
I registered my app already and it has been working just fine for years. It is only now that I'm trying to pull a list of Workspaces via the API that it's giving me the unauthorized error.
Also, as I mentioned above, I have already looked at those posts and they do not address my issue. I'm not pulling Tenant info.
Maybe you need some kind of special permissions to be able to access Workspace level classes, but if that's the case, I don't know where to go to get that permission.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I don't quite follow. The "Admin consent required" field says "No", just like it does for Dataset.ReadWrite.All (which is working just fine). Why would I need admin consent for Workspace when it says I don't need it, and when Dataset also says I don't need it (and it's working)?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I think the call you are referencing is only applicable to Premium environments.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Is there any way to confirm this? I don't see it mentioned in the docs I linked to. I'd like to make sure it's a limitation before I abandon this.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Shared capacity or Premium?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Shared.
Helpful resources

Power BI Dataviz World Championships
The Power BI Data Visualization World Championships is back! Get ahead of the game and start preparing now!

| User | Count |
|---|---|
| 3 | |
| 2 | |
| 1 | |
| 1 | |
| 1 |
| User | Count |
|---|---|
| 11 | |
| 7 | |
| 4 | |
| 3 | |
| 3 |