FabCon is coming to Atlanta
Join us at FabCon Atlanta from March 16 - 20, 2026, for the ultimate Fabric, Power BI, AI and SQL community-led event. Save $200 with code FABCOMM.
Register now!- Power BI forums
- Get Help with Power BI
- Desktop
- Service
- Report Server
- Power Query
- Mobile Apps
- Developer
- DAX Commands and Tips
- Custom Visuals Development Discussion
- Health and Life Sciences
- Power BI Spanish forums
- Translated Spanish Desktop
- Training and Consulting
- Instructor Led Training
- Dashboard in a Day for Women, by Women
- Galleries
- Data Stories Gallery
- Themes Gallery
- Contests Gallery
- QuickViz Gallery
- Quick Measures Gallery
- Visual Calculations Gallery
- Notebook Gallery
- Translytical Task Flow Gallery
- TMDL Gallery
- R Script Showcase
- Webinars and Video Gallery
- Ideas
- Custom Visuals Ideas (read-only)
- Issues
- Issues
- Events
- Upcoming Events
The Power BI Data Visualization World Championships is back! Get ahead of the game and start preparing now! Learn more
- Power BI forums
- Forums
- Get Help with Power BI
- Developer
- Need help - Embedding RLS in GenerateTokenRequest...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Need help - Embedding RLS in GenerateTokenRequestV2Report - BadRequest
Hello,
First time posting!
I'm having troubles when trying to add RLS in my Power Bi embedding application.
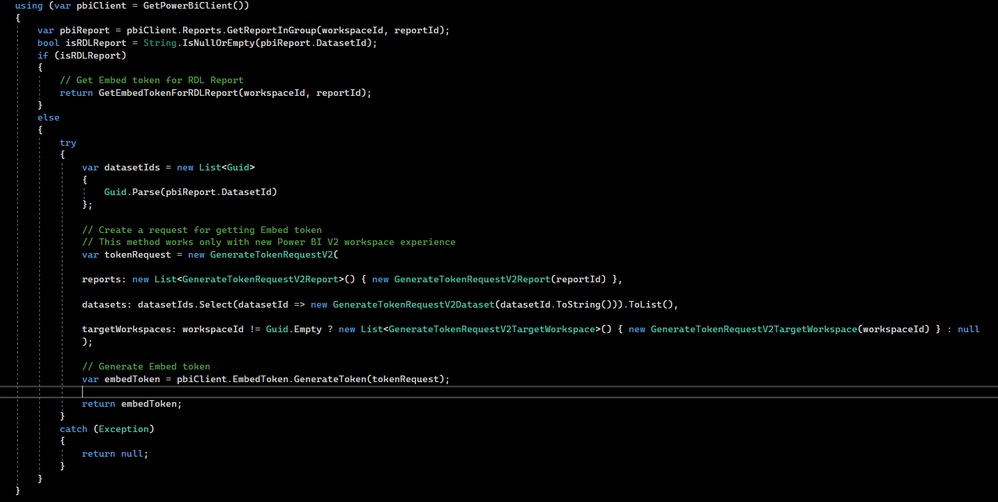
This is how my application was working before trying to add RLS
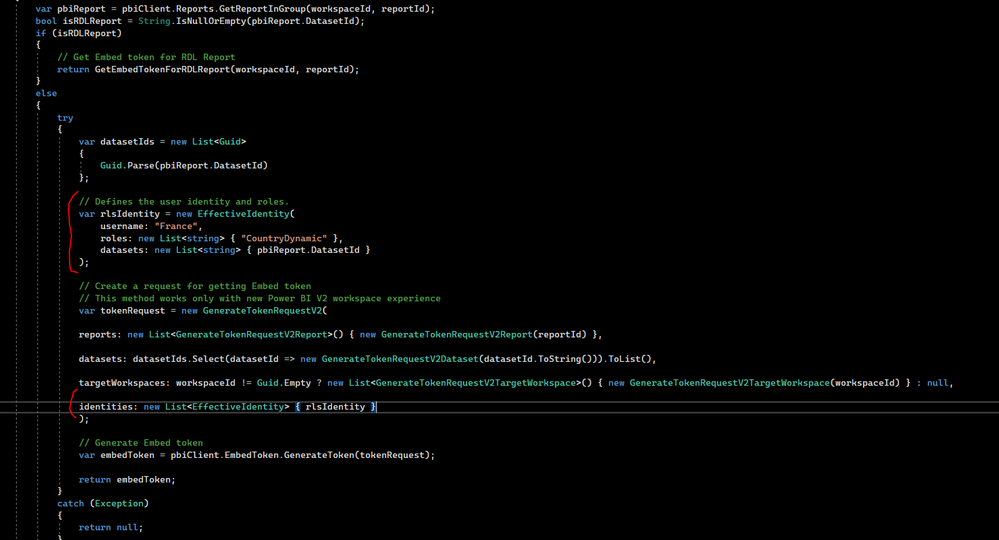
I then tried to do the following
(Side note : the username and roles are just testing, I'm not sure what I'm going to put there yet, I just want to see the token generate again)
This code not BadRequest errors on the pbliClient.EmbedToken.GenerateToken(tokenRequest); line
Does anyone have any ideas of where I'm going wrong? I'm new to PowerBi Embedding
Thanks for your time,
James
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you for your reply!
Any idea why I might be getting that BadRequest error though?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @JamesMinton ,
With Row Level Security (RLS), the identity you use can be different from the identity of the service principal or master user you're using to generating the token. By using different identities, you can display embedded information according to the user you're targeting. For example, in your application you can ask users to sign in, and then display a report that only contains sales information if the signed in user is a sales employee.
If you're using RLS, you can sometimes leave out the user's identity (the EffectiveIdentity parameter). When you don't use the EffectiveIdentity parameter, the token has access to the entire database. This method can be used to grant access to users such as admins and managers, who have permission to view the entire dataset. However, you can't use this method in every scenario. The table below lists the different RLS types, and shows which authentication method can be used without specifying a user's identity.
Here is the considerations and limitation applicable to each RLS type.
Besides, you can find some examples here: Embed Token - Generate Token - Examples| Microsoft Learn
For more details, please refer to:
Security in Power BI embedded analytics - Power BI | Microsoft Learn
Best Regards,
Jianbo Li
If this post helps, then please consider Accept it as the solution to help the other members find it more quickly.
Helpful resources

Power BI Dataviz World Championships
The Power BI Data Visualization World Championships is back! Get ahead of the game and start preparing now!

| User | Count |
|---|---|
| 9 | |
| 6 | |
| 4 | |
| 4 | |
| 3 |